


Remote work is no longer a temporary trend driven by the pandemic. It has stabilized as a enterprise VPN gateways global operating model.
According to large-scale workforce studies, employees worldwide now work remotely about one to two days per week, accounting for roughly 25–30% of total workdays, and this level has remained stable since 2023 .
As organizations operate across regions, cloud platforms, and time zones, one requirement has become universal: secure and continuous remote access. For many enterprises, that access still relies on VPN-based remote access — a design choice that is increasingly being questioned as remote work becomes permanent.
Global Remote Work Has Permanently Expanded the Remote Access Attack Surface
Remote and hybrid work is now embedded in enterprise operations. Recent surveys show that more than half operate under hybrid models , reflecting a structural shift rather than a temporary adjustment .
From a security standpoint, this matters because employees now connect from home networks, shared workspaces, hotels, and mobile networks — environments largely outside corporate control. What was once an occasional access path has become always-on infrastructure, continuously exposed to the public internet.
As a result, remote access security has become one of the most persistently exposed layers of enterprise IT.
VPN Security Risks: Why VPN Gateways Keep Appearing in Security Incidents
Threat intelligence and incident response reports consistently point to the same pattern: VPN gateways and VPN credentials remain one of the most common initial access vectors in modern attacks.
Industry data indicates that 78% of organizations experienced at least one security incident related to remote work in 2025, and 38% of attacks specifically targeted remote infrastructure , including VPNs and other remote access tools .
Once attackers gain access through a VPN — whether via stolen credentials or a vulnerable gateway — they often obtain a foothold that enables deeper movement into internal systems.
This is why security researchers increasingly describe VPNs not just as transport mechanisms, but as high-value access chokepoints.
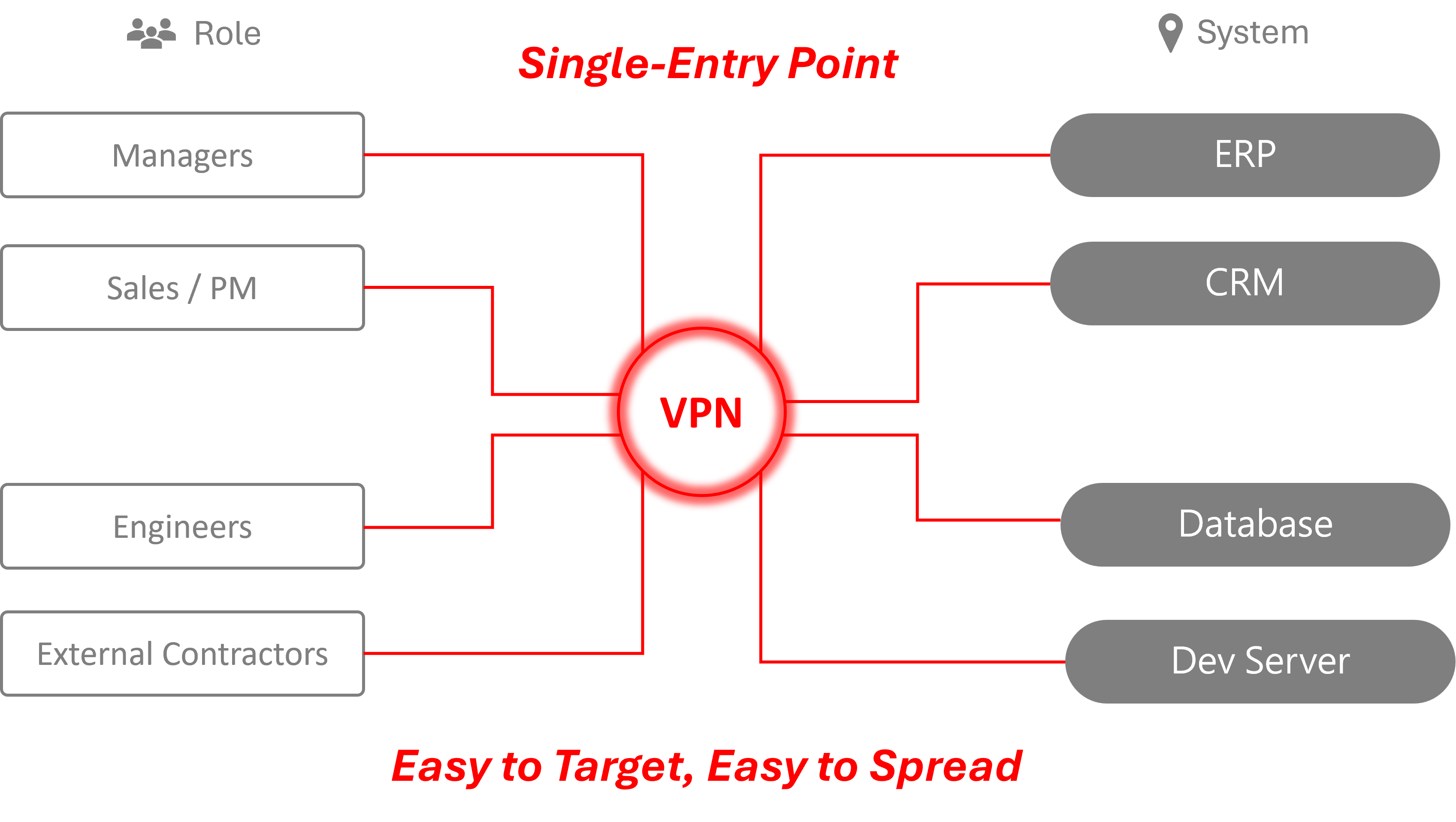
The Structural Security Limitations of Centralized VPN Architecture
Traditional VPN-based remote access relies on a centralized model:
A fixed, internet-facing gateway
Authentication performed at connection time
Network-level access granted after login
This architecture creates structural risk. A single gateway is easy to locate, easy to scan repeatedly, and — once compromised — capable of exposing far more than a single application or service.
Security research has shown that the widespread adoption of remote work triggered a 238% increase in VPN-targeted attacks between 2020 and 2022, highlighting how centralized VPN infrastructure scaled risk alongside usage .
The issue is not a specific vendor or vulnerability. It is the centralized trust model itself.
Why Patching VPNs Is Necessary — but Not Sufficient
Organizations typically respond to VPN-related incidents by:
Applying security patches
Updating firmware
Increasing monitoring and alerting
These steps are essential, but they address known weaknesses , not the underlying exposure model.
As long as remote access depends on:
Permanently exposed VPN portals
Centralized gateways as primary access points
Broad, network-level trust after authentication
the overall risk profile remains largely unchanged. This is why many security leaders now describe VPN risk as systemic rather than episodic.
Remote Access Security in 2026: Reducing Exposure and Limiting Blast Radius
The cost of remote-access-related breaches underscores why this reassessment is happening. Studies show that the average cost of a remote work–related security incident reached approximately USD 4.56 million in 2025, reflecting both direct response costs and long-term business impact .
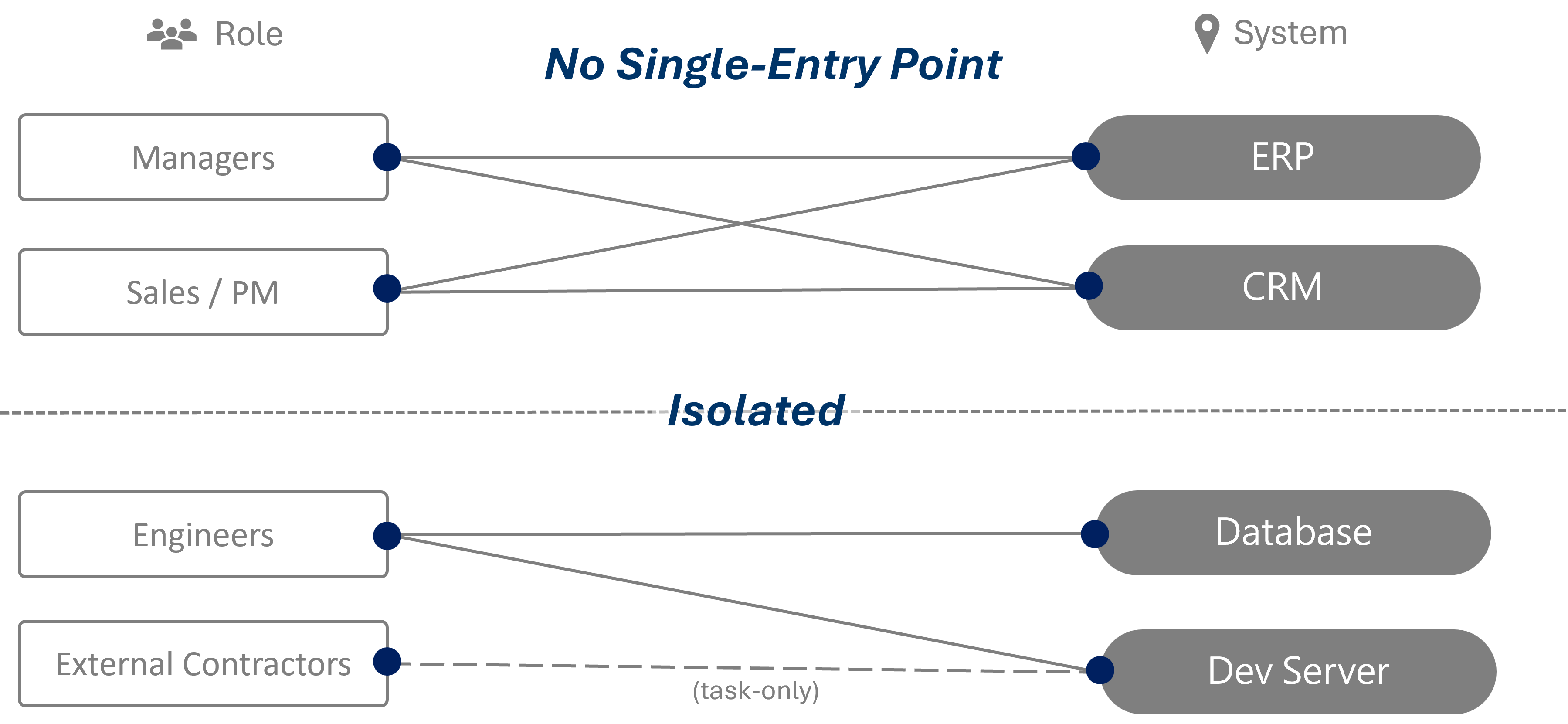
In response, organizations are increasingly shifting focus from “how to secure the VPN” to how to reduce the damage when access is abused. Modern remote access security strategies emphasize:
Minimizing exposed entry points
Scoping access to specific users, devices, and services
Enforcing isolation at the session level
Preventing lateral movement by design
These principles align closely with zero trust remote access , where trust is continuously evaluated and narrowly granted.
VPN vs. Zero Trust Remote Access: A Practical Security Tradeoff
With VPN-based access, authentication often results in broad internal visibility. With zero trust–oriented access models, connectivity is explicit, limited, and contextual.
For organizations supporting a distributed workforce, this distinction is critical. One approach concentrates risk at a single gateway; the other distributes access and constrains impact, even when credentials are compromised.
This is not about abandoning VPNs overnight — but about recognizing that VPNs were designed for a world where remote access was occasional, not constant.
What This Means for Organizations Moving Forward
Remote work is now global, persistent, and operationally essential. Security architectures built for a different era are under increasing strain.
As enterprises continue to support cross-border teams and cloud-native workflows, evaluating device-aware, session-isolated remote access models is becoming a logical next step in reducing long-term risk.
Conclusion
Remote work is now permanent and global. As remote access becomes always-on infrastructure, security models built around centralized VPN gateways are increasingly misaligned with modern threat realities.
Rather than hardening a single entry point, many organizations are shifting toward device-aware, session-isolated access models that reduce exposure and limit blast radius by design.
This architectural approach is also reflected in products like OrpheLink and OrpheAgent , which enable secure, direct connections without requiring changes to existing network environments.