

In early December 2025, threat intelligence teams reported a sharp increase in malicious activity targeting enterprise VPN gateways , particularly SSL VPN login portals exposed to the public internet.
Within days, scanning volume surged to over 2.3 million connection attempts against VPN authentication endpoints , representing a dramatic escalation compared to normal background noise.
This pattern signals more than a short-lived spike. It reflects a broader shift in how attackers view VPN gateways: not as defensive tools, but as strategic entry points into enterprise environments.
This Isn’t About One Vulnerability — It’s About the Role VPN Gateways Now Play
VPNs were originally designed to extend secure access beyond the corporate perimeter. As long as the gateway itself remained hardened, the internal network was assumed to be protected.
That assumption no longer holds.
Today, VPN gateways are continuously deployed as fixed, internet-facing access points. From an attacker’s perspective, this makes them predictable, observable, and worth sustained attention. Rather than waiting for a single exploit, attackers increasingly rely on:
Continuous automated scanning
Long-term reconnaissance of authentication endpoints
Repeated probing for both known and emerging weaknesses
The risk is no longer tied to a specific flaw. It is tied to the strategic importance of the product itself.
The Structural Security Risks of Centralized VPN Gateway Architectures
Across multiple incidents, centralized VPN and gateway products tend to share architectural traits that amplify risk under modern threat conditions.
Fixed Public Entry Points
VPN login portals are designed to be reachable. Once discovered, they remain exposed indefinitely and are routinely indexed by attacker infrastructure.
Single Devices with Disproportionate Trust
Authentication, encryption, session control, and network access often converge on a single gateway. Compromise at this point impacts far more than one session.
Broad Access After Authentication
Many VPN deployments still grant network- or subnet-level access after login, enabling rapid lateral movement once a foothold is established.
These risks are not vendor-specific. They stem from centralized access models built around a single trusted gateway.
Why Patching Alone Doesn’t Change the Risk Profile
Security teams respond to incidents by patching, upgrading firmware, and increasing monitoring. These steps are essential, but they only address known weaknesses.
They do not change the underlying exposure model.
As long as organizations rely on:
Permanently exposed VPN portals
Centralized gateways as the primary access control point
Network-level trust after authentication
they remain dependent on a model that concentrates risk rather than distributing it.
When Legacy Access Assumptions Collide with Modern Threat Models
Traditional VPN architectures were built on a simple premise: secure the perimeter, and the network stays safe.
Modern attack behavior has eroded that premise. In an environment where reconnaissance is constant and automated, any always-on, high-privilege access point becomes a long-term target.
This is no longer a debate about performance or feature sets. It is about whether centralized remote access architectures are compatible with today’s threat landscape.
Recent events reinforce a growing conclusion across the industry: VPN gateways are increasingly a high-risk component in modern remote access strategies.
From Isolated Incidents to Architectural Reassessment
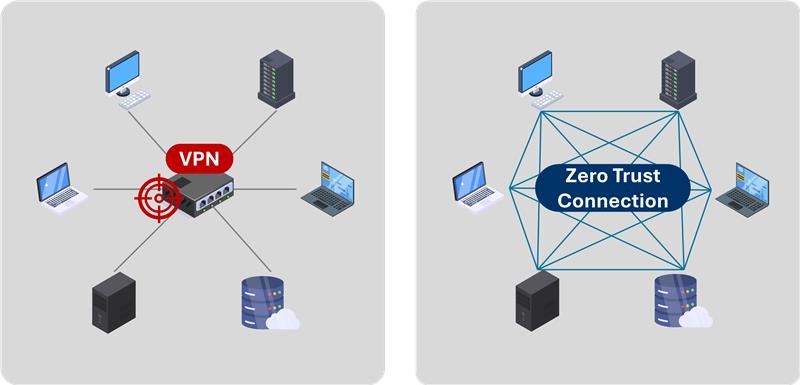
Centralized VPN gateways create a single, high-value attack target, while zero trust connections distribute access and limit lateral movement by design.
As a result, many organizations are re-evaluating whether VPN gateways should remain the default mechanism for remote access.
The discussion is shifting toward architectural principles such as:
Eliminating fixed, high-value entry points
Limiting access scope to individual devices and sessions
Enforcing isolation by design, rather than containing breaches after the fact
This shift is not about abandoning tools. It reflects the reality that access models must evolve alongside threat models.
Reducing Risk by Removing the Target
OrpheLink is designed around this architectural shift.
Instead of reinforcing a single gateway, it removes the conditions that make any one component a persistent attack focus. By establishing device-level, session-isolated connections, access becomes distributed, controlled, and inherently constrained.
In practice, this approach reduces the systemic risk that centralized VPN gateways introduce in real-world environments.
Further Reading