

Why Traditional VPN Architectures Are Facing Their Biggest Challenge in a Decade
For years, VPNs have served as the primary gateway for enterprise remote access, encrypting traffic and allowing employees to connect back to internal systems from outside the corporate network.
But today, the very devices designed to protect enterprise networks are increasingly becoming high-value attack targets. Traditional VPN architectures are now facing their most serious structural security challenges in over a decade.
Why VPN Gateways Are Constantly Scanned and Exposed to the Internet
Following the global shift to hybrid work after COVID-19, enterprise networks have dramatically expanded their external attack surface. Public-facing VPN portals have become easier to identify, easier to scan, and increasingly attractive to attackers.
Recent threat intelligence shows that large-scale, systematic scanning of VPN gateways is no longer an anomaly — it is a persistent and intentional activity. These scans are not random background noise. They are targeted reconnaissance campaigns designed to map exposed VPN endpoints and prepare for future exploitation.
Even when no vulnerability is immediately exploited, continuous scanning often signals:
Newly disclosed or emerging vulnerabilities
Pre-exploitation reconnaissance
Inventory collection ahead of weaponization
Once a VPN gateway is identified and monitored, it tends to remain on attackers’ long-term target lists.
VPN Gateways as a Common Initial Access Point in Modern Attacks
Multiple security research reports over the past year indicate a clear trend:
VPNs are now one of the most common initial access points in modern attacks,
including ransomware campaigns.
Key findings consistently show that:
A significant portion of breaches originate from compromised VPN credentials or exposed VPN portals
Many intrusions leverage known but unpatched VPN gateway vulnerabilities
Any VPN portal exposed to the internet and discoverable via scanning is likely to face sustained probing
This marks a shift from opportunistic exploitation toward persistent reconnaissance , where VPN gateways are treated as reliable, repeatable entry points rather than one-off targets.
The Security Risks of Centralized VPN Architecture
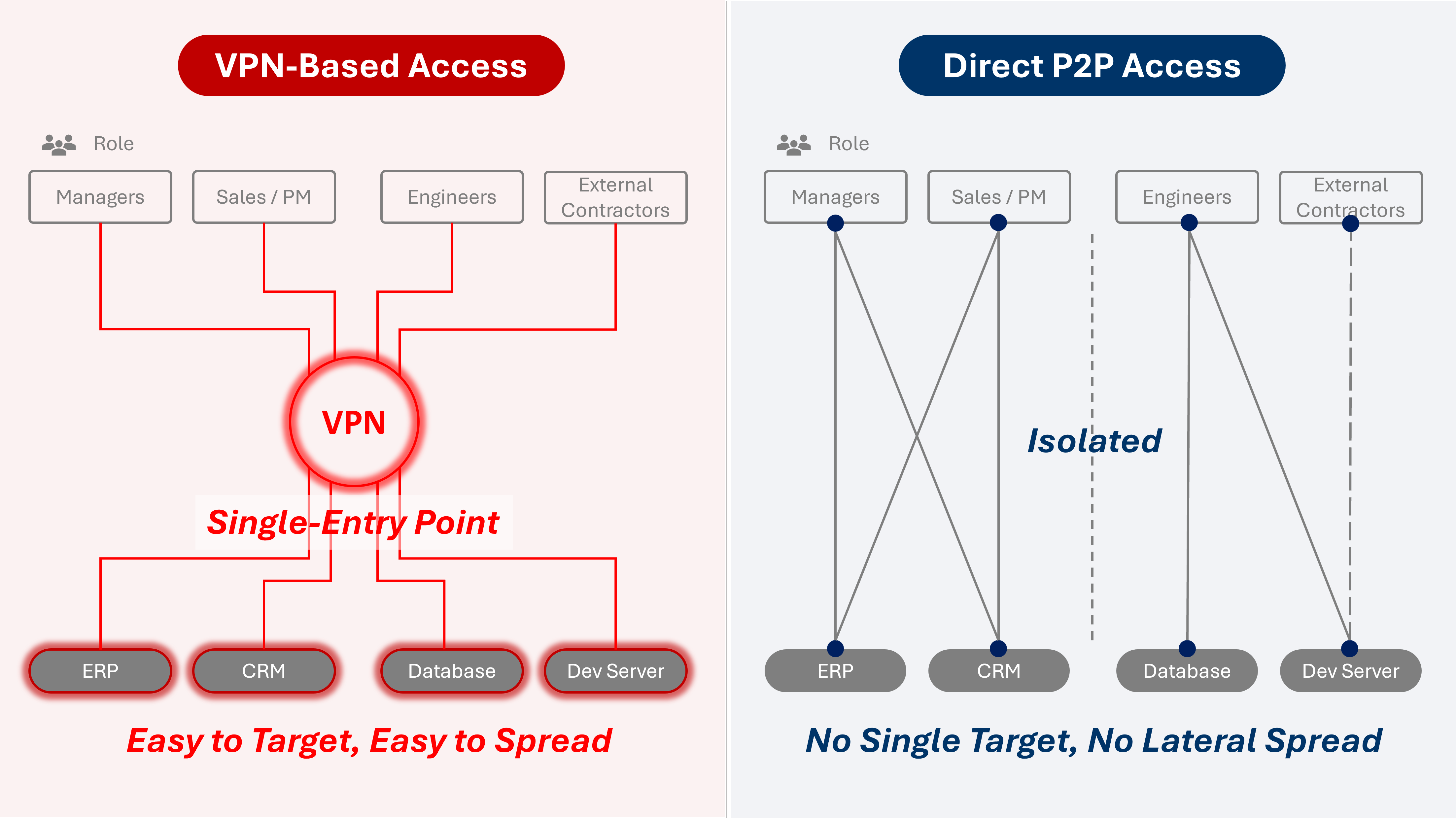
VPN-based access introduces a centralized gateway that is continuously exposed to scanning and exploitation. Once compromised, attackers can move laterally across internal systems. Endpoint-centric access eliminates this single entry point by establishing isolated, direct connections.
From an architectural perspective, traditional VPN deployments share several defining characteristics:
A single, fixed, and publicly reachable entry point (the VPN gateway)
Authentication primarily based on credentials, certificates, or sessions
Post-authentication access to broad internal network segments
Network-level trust once the tunnel is established
These design choices made sense 15–20 years ago. In today’s threat landscape, however, they create a static and highly visible attack surface.
Once compromised, a centralized VPN gateway often enables:
Lateral movement across internal networks
Privilege escalation beyond the initial access scope
Rapid expansion of attack impact
Because enterprise VPN deployments are often architecturally similar, attackers can reuse techniques across organizations with high efficiency.
Why Traditional VPNs Struggle in Hybrid and Cloud Environments
Between 2020 and 2025, enterprise IT environments have undergone fundamental changes:
Users and devices are globally distributed
SaaS, IaaS, and PaaS platforms are now primary work environments
Applications and data are no longer confined to a single internal network
Access requirements span clouds, regions, and endpoints
In this context, network-centric VPN models increasingly clash with application-centric and identity-centric workflows. What was once a secure perimeter has become a bottleneck — and, in many cases, a liability.
Rethinking VPN-Based Access for Modern Security Architecture
In security architecture reviews, RFPs, and procurement discussions, organizations are now asking fundamental questions:
Can a public VPN portal avoid becoming the next attack surface?
Is lateral movement risk after VPN login acceptable?
Can VPNs scale safely across hybrid and multi-cloud environments?
Do we need more granular authorization than network-level access?
These questions do not suggest that VPNs will disappear overnight. They do indicate, however, that the gap between traditional VPN architecture and modern threat models is rapidly widening.
VPNs are increasingly viewed not as a first line of defense, but as high-risk boundary devices that demand careful reconsideration.
Rethinking Secure Access Architecture — Not Just Replacing Tools
The evolving risk profile of VPNs highlights a broader shift in security thinking. The focus is moving away from strengthening a single gateway and toward reducing exposure, minimizing blast radius, and eliminating single points of failure.
As a result, more organizations are exploring secure access models that emphasize:
Fine-grained identity and authorization controls
Decentralized, distributed connectivity
Zero-trust access without fixed, public entry points
In an era where continuous scanning and targeted reconnaissance are the norm, architectural change — not incremental patching — is becoming unavoidable.
Organizations that reassess their access architecture early will be far better positioned to defend against persistent, well-resourced adversaries in this new security reality.
This shift is driving growing interest in device-level, connection-based secure access models that move away from centralized VPN gateways and toward more isolated, controllable connectivity.
Learn how OrpheAgent builds a secure remote access architecture centered on remote endpoints.